The Hackers News |
- Official Website of Amy Winehouse - Songer/Songwriter Defaced by #Antisec
- Meggit - US Military and Law Enforcement equipment supplier hacked for #Antisec
- Mesa Arizona Fraternal Order of Police website hacked, Data exposed !
- SQL Injection Vulnerability in Google Lab Database System
- MasterCard downed by ISP, not Anonymous hackers
- Indonesian and Australian police launched Cyber Crime Investigation Center
- OpenSSH 3.5p1 Remote Root Exploit for FreeBSD
- Mobius Forensic Toolkit v0.5.8 Released
- TDSS rootkit infects 1.5 million US computers
- FBI searches LulzSec suspect home in Hamilton, Ohio
| Official Website of Amy Winehouse - Songer/Songwriter Defaced by #Antisec Posted: 01 Jul 2011 12:33 AM PDT Official Website of Amy Winehouse - Songer/Songwriter Defaced by #Antisec Amy Jade Winehouse official website http://www.amywinehouse.com/ defaced by Anonymous hackers for Antisec . Amy Jade Winehouse (born 14 September 1983) is an English singer-songwriter, known for her powerful contralto vocals and her eclectic mix of various musical genres including R&B, soul, and jazz. She has received publicity over her substance abuse and mental health issues. Related hack => Meggit - US Military and Law Enforcement equipment supplier hacked for #Antisec - Read here |
| Meggit - US Military and Law Enforcement equipment supplier hacked for #Antisec Posted: 01 Jul 2011 12:20 AM PDT Meggit Database Hacked - US Military and Law Enforcement equipment supplier for #Antisec Database of www.meggitttrainingsystems.com a US Military and Law Enforcement equipment supplier has been hacked and exposed by Anonymous ( The Bash Crew ) . Hackers said "People of the USA your government puts there trust and your money into these people and we got into there database useing a google dork and a simple sql injection.Any ways we hope this will cause many lulz atleast in spamming heads of the corp's and government that choose such a poorly secured site. " vUNL link : http://www.meggitttrainingsystems.com/main.php?id=119 Hackers Release database on Pastebin : http://pastebin.com/0r4A9DVR |
| Mesa Arizona Fraternal Order of Police website hacked, Data exposed ! Posted: 30 Jun 2011 09:23 PM PDT Mesa Arizona Fraternal Order of Police website hacked, Data exposed ! Anonymous Hackers deface Mesa Arizona Fraternal Order of Police website - http://mesafop.com/ . This hack is done for Operation Antisec. The Post a message and All data of Arizona Police on the deface page. Alternate you can see written part on : http://pastebin.com/RakyZgJE . Hackers claim to deface following domains : azfop.com, azfop78.com, azfop5.com, tucsonfop.com, mesafop.com,azfop32.com, azfop50.com, azfop44.com, azfop62.com, azfop58.com Hackers expose Credit Card details and Email/Passwords of lots of officers Not only this, They also expose the usernames and passwords for 1200 FOP members in deface page. |
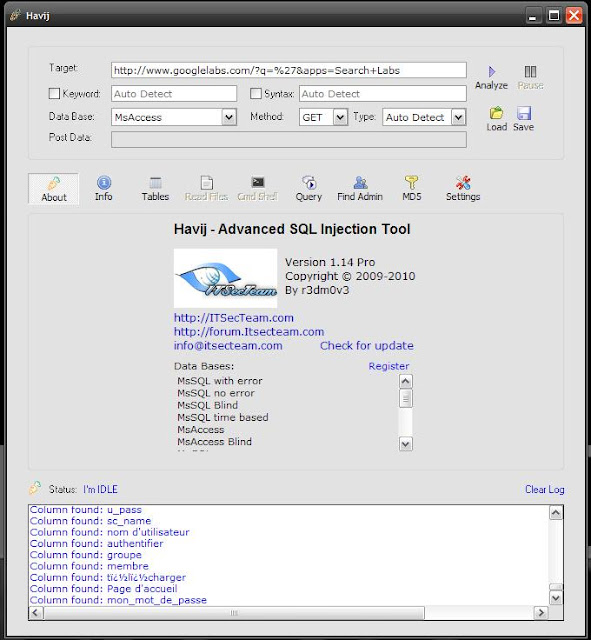
| SQL Injection Vulnerability in Google Lab Database System Posted: 01 Jul 2011 12:41 AM PDT SQL Injection Vulnerability in Google Lab Database System Very Big & Critical Vulnerability detected in Google Lab System. Vendor is already reported by hackers, But they don't take positive step in this case, so finally hackers exposed the vulnerability in public by Bangladesh Cyber Army Admin - Shadman Tanjim on their Forum. Google Lab Website has SQL Injection Vulnerability and Dangerous thing is this Vulnerability is Exploitable. Hackers are able to get Tables, columns and data from Database. Google Lab Database has his own customize DB system. But Interesting things is their database system is Similar as Ms Access database. In this case Ms Access SQL Injection System is Also Work on Google Lab Database system. Statement By Hacker : I already contact with Google Corporation but they don't give positive response, I think this is their big fault, and will suffer for that. But if they give Positive response then this will be very good for them. Thanks a Ton!!! Shadman Tanjim Ethical Hacker, Programmer and Security Professional Email: admin@bdcyberarmy.com or shadman2600@gmail.com Website: www.bdcyberarmy.com/forum Greets to: Shahee Mirza, Almas Zaman, Sayem Islam, Pudina pata, LuckyFm and All Bangladesh Cyber Army Members. Video Download link: http://www.bdcyberarmy.com/Google/google_video.avi Hackers Release Step by step proof about this Vulnerability 1. Website : www.googlelabs.com or labs.google.com 2. Vulnerability type : SQL Injection 3. Vulnerable url : http://www.googlelabs.com/?q=%27&apps=Search+Labs 4. Info: Host IP: 209.85.175.141 Web Server: Google Frontend Keyword Found: Fast Injection type is Integer Let's Check Exploiting this Vulnerable link. Here Hackers use 3 Famous SQL Injection tools. They are: 1. Havij Advance SQL Injection Tool 2. Safe3 SQL Injector v8.4 3. Pangolin SQL Injection Tool 1st Work with Havij Advance SQL Injection Tool: Screen Shot 1: Scan Vulnerable link and it says this website is Vulnerable. Screen Shot 2: Now it scans and gets all tables and columns Screen Shot 3: Now you can see list of tables and Columns And this is a Prove for this Website is Genuine SQL Injection Vulnerable. Here you see this database type is MS Access, so this is a Proof of this concept. Some people should Say Google Lab Database System is not Ms Access but this Website Database is Similar as Ms Access database and Ms Access SQL Injection Query are also Work on Google Labs Database system. As like MySQL 5 and MySQL 4.1 both are injected via Union select, but both are not have Information Schema. 2nd now Work with Safe3 SQL Injector v8.4: Screen Shot 1: Analyzing Vulnerable link and it says it's vulnerable and gets keyword and db type. Screen Shot 2: Now it's Inject the vulnerable link and gets All Table list and column list This is another Prove for this Website Vulnerability and we can see this and Dangerous thing is its Exploitable. Now we check our last SQL Injection tool for 100% Satisfy. 3rd Pangolin SQL Injection Tool: Screen Shot 1: Scan vulnerable link and its say this website is vulnerable Screen Shot 2: Now inject this Website and get tables and columns list Screen Shot 3: Here is a full List of Tables and Columns list Now I think we are 100% Sure Google Lab Website is SQL Injection Vulnerable. You Can Check Video. This Video is also made by Bangladesh Cyber Army Member - Shadman Tanjim. UPDATE : Google insist that there has been no intrusion. The company claims that their GQL database won't allow SQL injection attacks. Additionally, they say that the data that appears in the screen shots, does not exist anywhere in their data stores. On this Shadman Tanjim - Hackers Reply to Google "Proof it. because I am Also Proof it's Vulnerable. If they say's Google Lab is Not Vulnerable, It Means We get new Bugs in Some Famous SQL Injection tools. And also and 1=1 concept. So tell them to proof this and I don't think All tools are false. because 1 tools can false, 2 tools can get false but not All. ALL Tools say's it is Vulnerable, So i don't think it any confusion. :D " |
| MasterCard downed by ISP, not Anonymous hackers Posted: 30 Jun 2011 09:20 AM PDT MasterCard downed by ISP, not Anonymous hackers Two days before Anonymous declare that MasterCard again down by Ddos attack in support of Wikileaks & Anonymous via twitter. It was shortly after MasterCard went down that someone on Twitter, known as ibomhacktivist, promoted "MasterCard.com DOWN!!!", adding the site was down for messing with WikiLeaks and Anonymous. But in actual, MasterCard.com was offline, and shortly after the outage was noticed by the public, someone on Twitter claimed credit. In a statement, MasterCard blamed the outage on an ISP issue, without discounting that they were attacked upstream. "MasterCard's corporate, public-facing Website experienced intermittent service disruption, due to a telecommunications/Internet Service Provider outage that impacted multiple users. It is important to note that no cardholder data has been impacted and that cardholders can continue to use their cards securely. We are continuing to monitor the situation closely.," spokeswoman Jennifer Stalzer said in an email to the media. |
| Indonesian and Australian police launched Cyber Crime Investigation Center Posted: 30 Jun 2011 09:00 AM PDT Indonesian and Australian police officially launched a joint project called the Cyber Crime Investigation Center. The center was officiated by Indonesian National Police chief Gen. Timur Pradopo and Australian Federal Police chief Comr. Tony Negus at the National Police Headquarters in Jakarta on Thursday. Timur said the center had been planned since six months ago. "Today, we launch the center, which will be equipped with tools needed to carry out cyber crime investigation," Timur said, adding that its communication technology equipment was being provided by the Australian government."Of course, this [center] will improve our capacity to detect and [investigate cyber] crimes, particularly transnational crimes," he said. Negus said the center would allow the Indonesian National Police to deal with technology and IT-related crimes. He added that the Australian police force was looking to forge cooperative agreements in its investigation of transnational crimes, not only in region but also across the world. |
| OpenSSH 3.5p1 Remote Root Exploit for FreeBSD Posted: 30 Jun 2011 08:10 AM PDT OpenSSH 3.5p1 Remote Root Exploit for FreeBSD OpenSSH 3.5p1 Remote Root Exploit for FreeBSD has been shared by kcope on twitter. The Released note is as given below : OpenSSH 3.5p1 Remote Root Exploit for FreeBSD |
| Mobius Forensic Toolkit v0.5.8 Released Posted: 30 Jun 2011 08:05 AM PDT Mobius Forensic Toolkit is a forensic framework written in Python/GTK that manages cases and case items, providing an abstract interface for developing extensions. Cases and item categories are defined using XML files for easy integration with other tool Change Log :
Installation As root, type: python setup.py install Usage Run mobius_bin.py. Download Here |
| TDSS rootkit infects 1.5 million US computers Posted: 30 Jun 2011 07:56 AM PDT TDSS rootkit infects 1.5 million US computers Millions of PCs around the world infected by the dangerous TDSS 'super-malware' rootkit as part of a campaign to build a giant new botnet. The report is presented by researchers from security firm Kaspersky Lab. TDSS also known as 'TDL' and sometimes by its infamous rootkit component, Alureon. It has grown into a multi-faceted malware nexus spinning out ever more complex and dangerous elements as it evolves. Kaspersky Lab researchers were able to penetrate three SQL-based command and control (C&C) servers used to control the activities of the malware's latest version, TDL-4, where they discovered the IP addresses of 4.5 million IP PCs infected by the malware in 2011 alone. Almost 1.5 million of these were in the US.If active, this number of compromised computers could make it one of the largest botnets in the world, with the US portion alone worth an estimated $250,000 (£155,000) to the underground economy. The researchers noticed a kad.dll component of the infection which appears to allow TDSS/TDL-4 an elaborate C&C channel to control bots using the Kad P2P file exchange network even if the primary encrypted channel has been shut down by rival botnetters or security companies. "We don't doubt that the development of TDSS will continue," said Kaspersky researcher, Sergey Golovanov, who performed the latest analysis of TDSS. "Active reworkings of TDL-4 code, rootkits for 64-bit systems, the use of P2P technologies, proprietary anti-virus and much more make the TDSS malicious program one of the most technologically developed and most difficult to analyse." |
| FBI searches LulzSec suspect home in Hamilton, Ohio Posted: 30 Jun 2011 07:39 AM PDT FBI searches LulzSec suspect home in Hamilton, Ohio The investigation into the LulzSec hacking team continues, with news that FBI agents have searched a house in Hamilton, Ohio. FBI investigation believed to have been fuelled by interviews with Ryan Cleary, but did not lead to charges. Federal agents are said to have searched a teenager's home in Jackson Road, Hamilton on Monday 27 June, although no-one was charged after the search warrant was served. Ohio teenager was known within LulzSec as "m_nerva", who leaked text logs of discussions between the group after they had hacked into the website of an FBI affiliate at the beginning of June. After that, m_nerva's case address was listed by LulzSec as being in Hamilton, Ohio  Last week FBI agents searched the house of a woman in Iowa and questioned her about links with the group. LulzSec said in a statement that it had six members, though it never stated their gender. Last week FBI agents searched the house of a woman in Iowa and questioned her about links with the group. LulzSec said in a statement that it had six members, though it never stated their gender. |
| You are subscribed to email updates from THN : The Hacker News To stop receiving these emails, you may unsubscribe now. | Email delivery powered by Google |
| Google Inc., 20 West Kinzie, Chicago IL USA 60610 | |